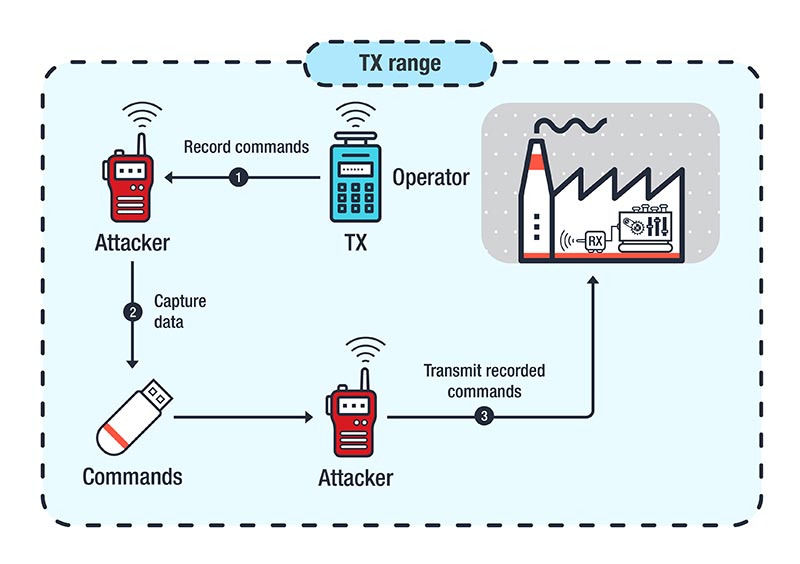
Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News - Trend Micro DK

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发
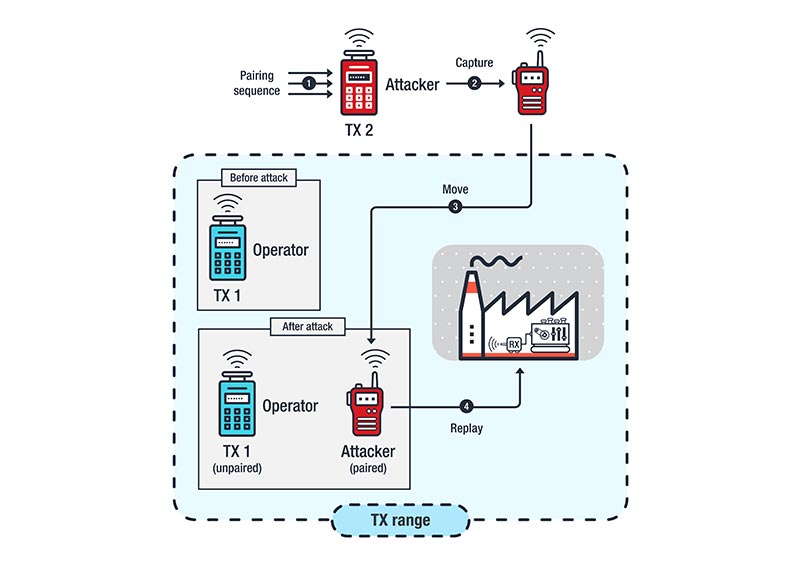
Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News - Trend Micro DK

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发

Introduction of 《Inside Radio: An Attack and Defense Guide》 – 雪碧0xroot | RadioHub | IoT RF Hardware Hacking | 博观而约取厚积而薄发

Sensors | Free Full-Text | Tracking the Insider Attacker: A Blockchain Traceability System for Insider Threats
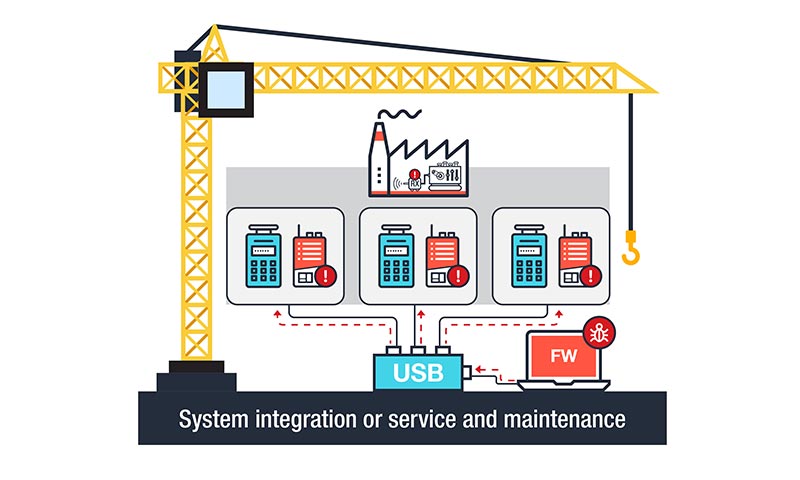
Attacks Against Industrial Machines via Vulnerable Radio Remote Controllers: Security Analysis and Recommendations - Security News - Trend Micro DK