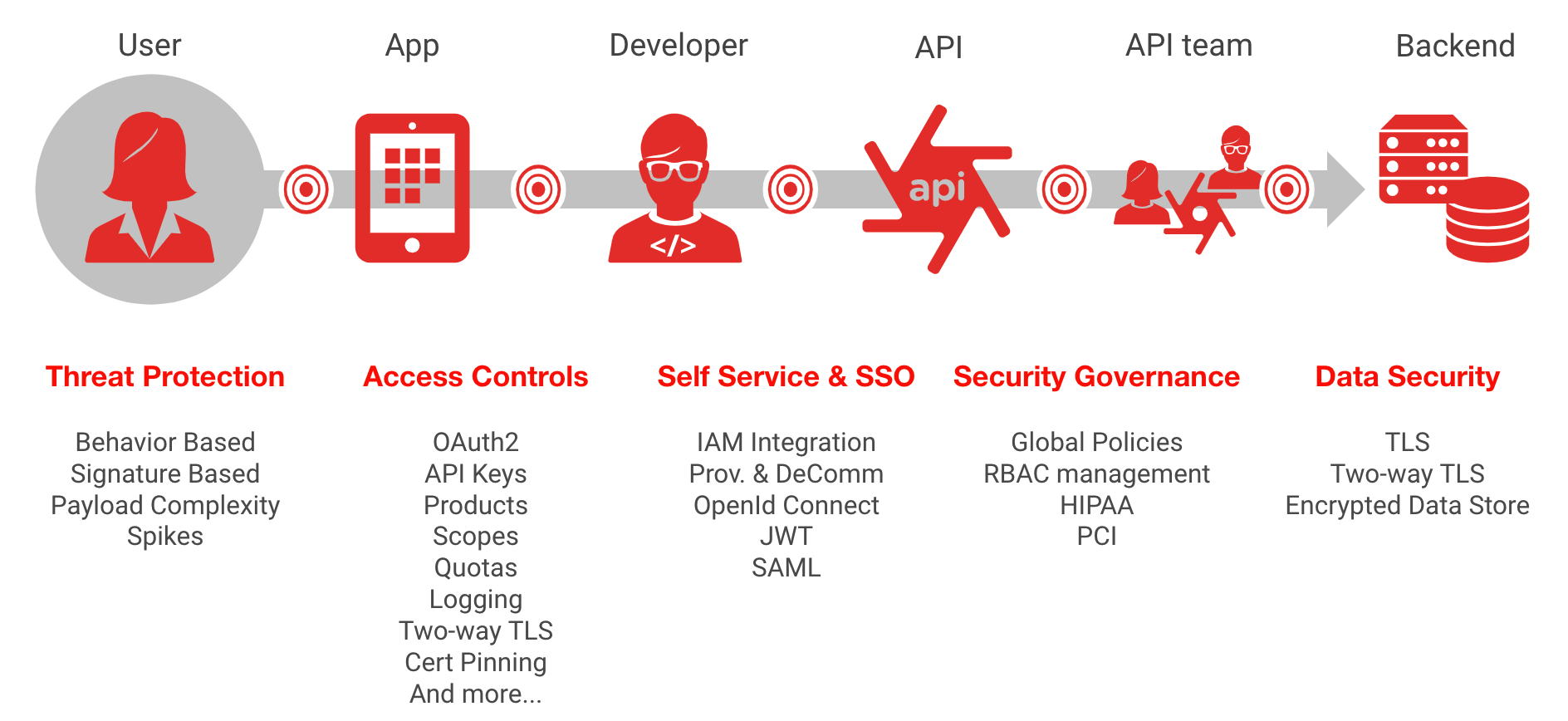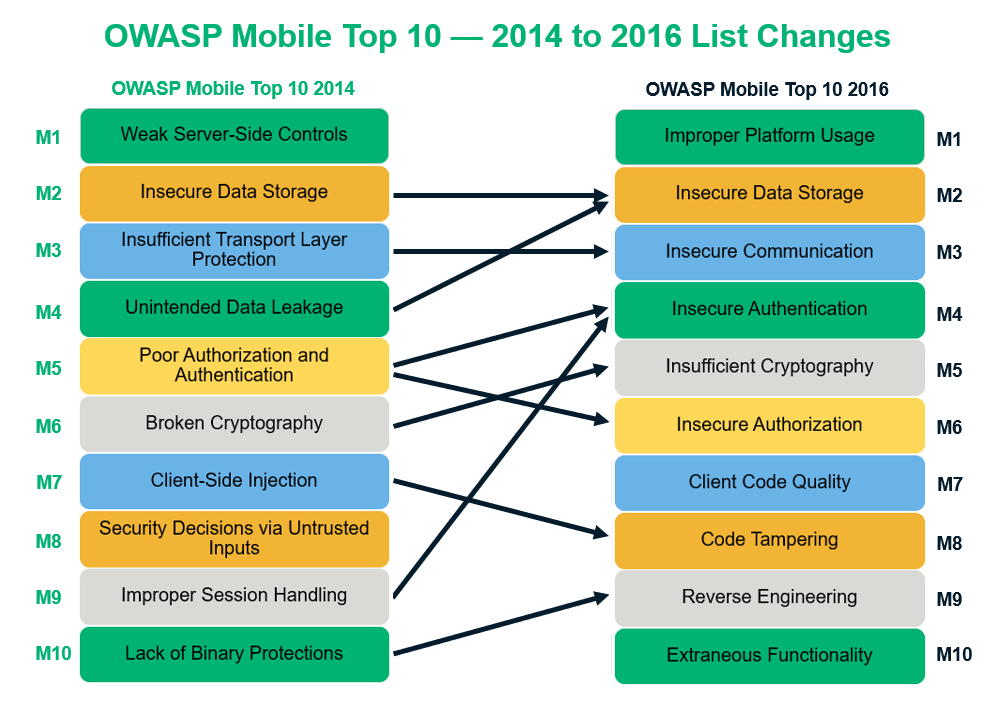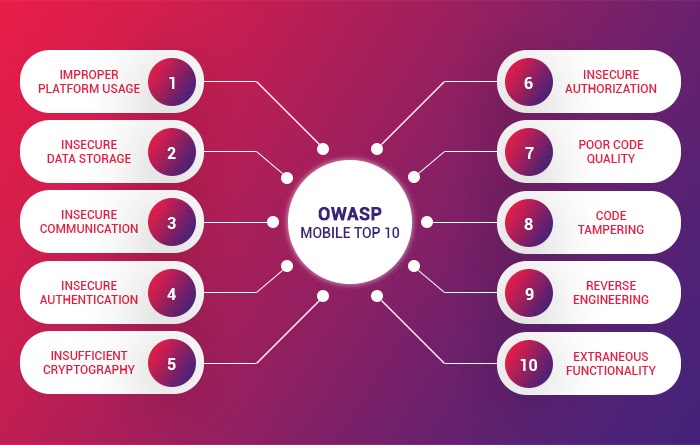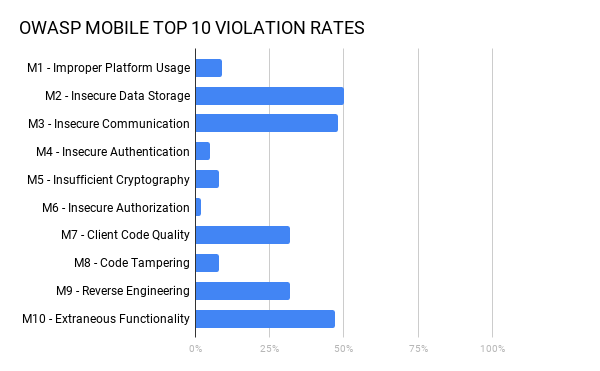
OWASP mobile top 10 security risks explained with real world examples | by Kristiina Rahkema | The Startup | Medium

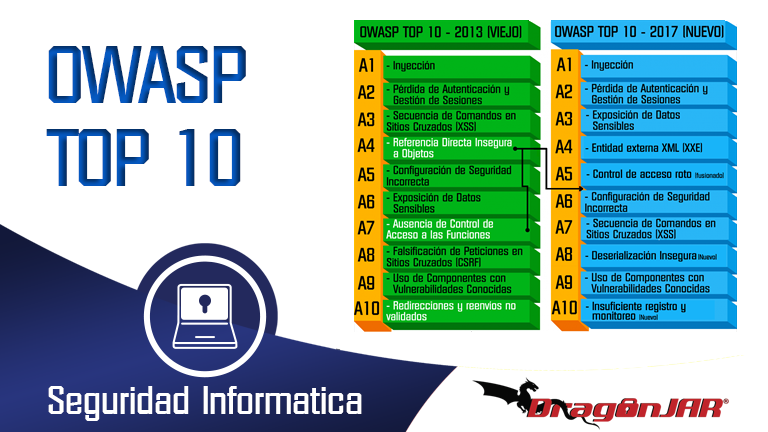
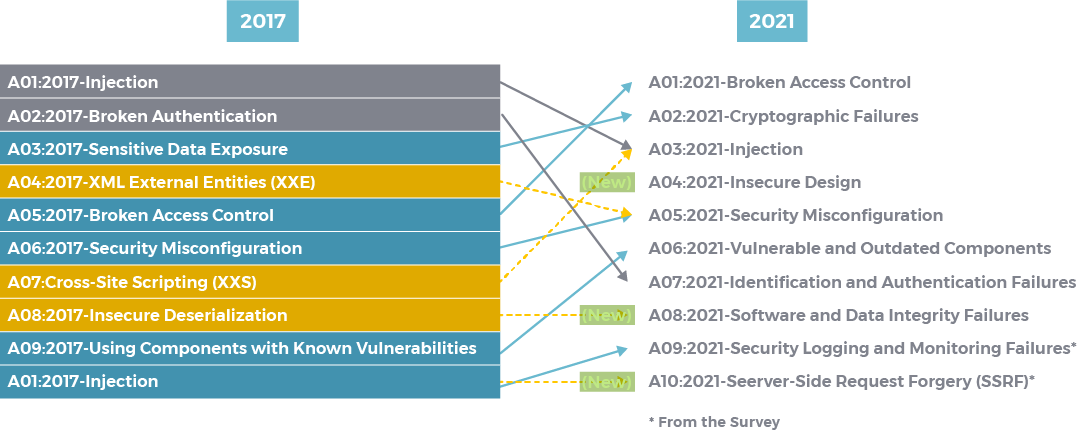
Projeto OWASP Top 10 2017: lançamento da versão apresenta duas novas categorias - SegInfo - Portal, Podcast e Evento sobre Segurança da Informação
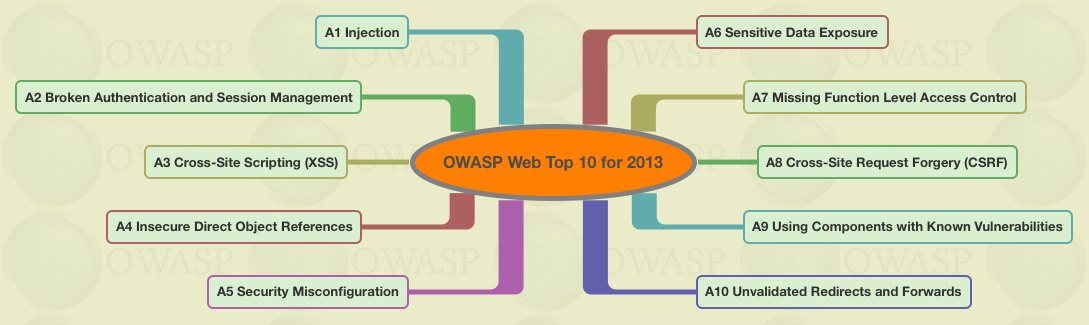
Vulnerability Analysis of E-voting Application using Open Web Application Security Project (OWASP) Framework